AI-powered striptease tools: The underlying technology and legal risks you should be aware of.
AI stripping toolIn recent years, it has become an internet sensation, relying onGenerative Adversarial Networks (GANs) and Deep LearningThe ability to "virtually remove clothes" from photos of people has sparked controversy.Ethics, privacy, technology and lawThe controversy is multifaceted. While most tools have been rigorously investigated and removed from app stores, phishing and malware incidents continue to rise.This article analyzes its principles, mainstream tools, legal risks, ethical dilemmas, fraud prevention suggestions, and security self-protection measures, urging users to stay away from illegal applications and protect their data security and digital dignity.

The Rise of AI-Powered Nude-Removing Tools: Current Status and Social Concern
The phenomenon and heated discussion surrounding AI-powered striptease tools
With the rapid development of artificial intelligence technologyAI-powered undressing tool (Undress AI)This has become a focus of social and media attention. These tools can virtually remove clothing from photographs of people, creating highly controversial images. Because...Ethical, privacy, cybersecurity and legal issuesThe related technologies continue to be hotly debated, and have even been used by criminals for fraud, extortion, and the spread of malicious software, causing significant harm.
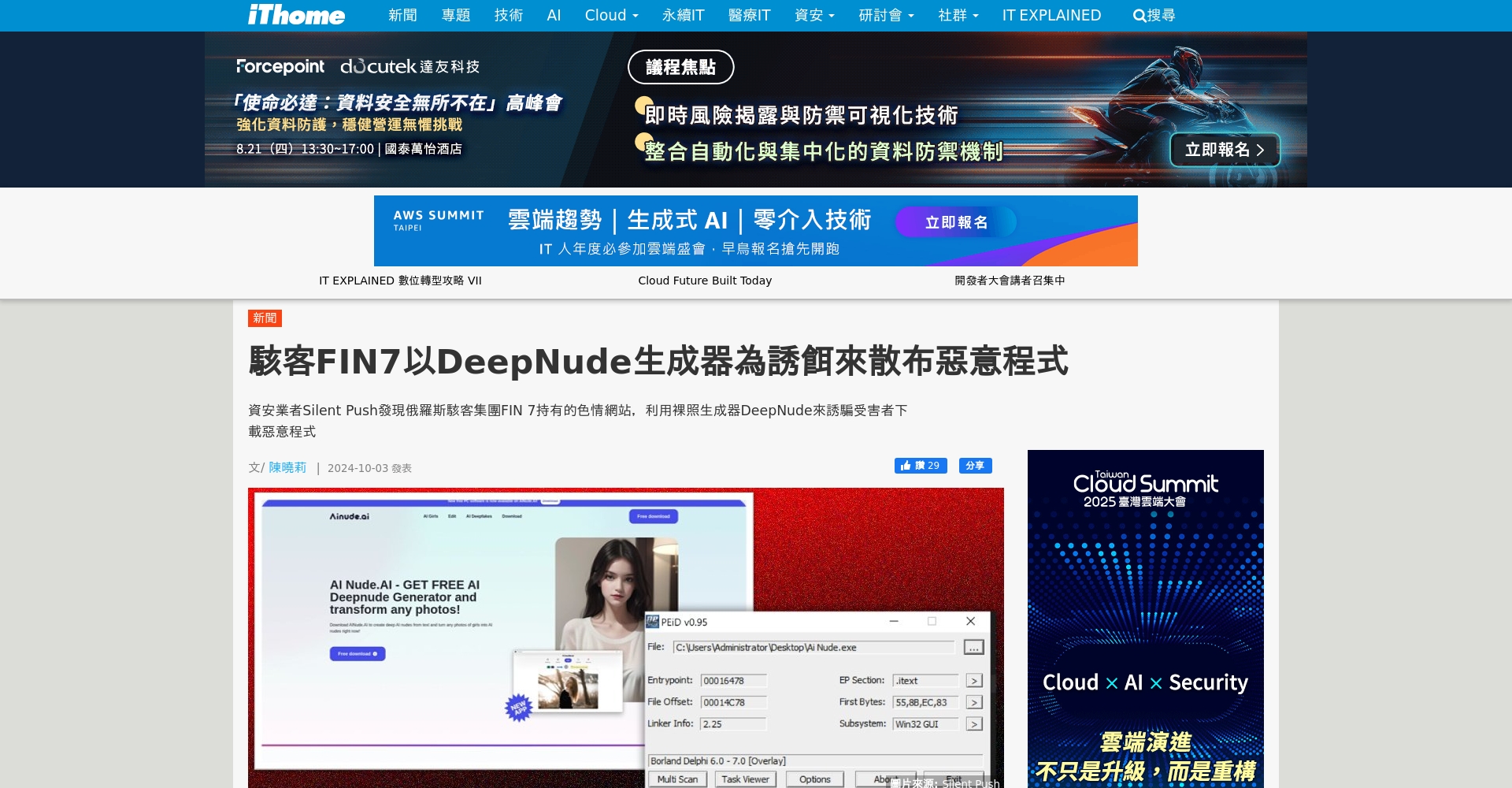
- The 2024 Silent Push report revealed that the Russian hacker group FIN7 established...Over 4,000 phishing websitesThey impersonated DeepNude to steal user data, passwords, and other information.Report Details
The technical principle of AI-powered clothes removal tools
Generative Adversarial Networks (GANs) and Deep Learning
The core of AI-powered stripping tools lies in Generative Adversarial Networks (GANs) and deep learning.GAN systems consist of a "generator" and a "discriminator," which, through repeated training, make the synthesized images closely resemble the real appearance.
| Technology Name | Basic principles | Main uses | Main risks |
|---|---|---|---|
| GANs | Dual-model competitive generation | Automatic drawing/compositing | Fake images, deep fraud |
| Stable Diffusion | Text/Image Generation | Role changes, detail completion | Content abuse, fake nude photos |
| Deep portrait segmentation | Foreground Segmentation | Remove clothing and other designated areas | Personal information leakage and infringement of portrait rights |
Taking DeepNude and Nudify as examples, they all combine facial recognition with body structure segmentation, plus...Training with a large number of labeled nude photosThis enables AI to "predict" the shape of a person after they have undressed.
Examples of common AI undressing tools
| Tool Name | Link | state | Main features |
|---|---|---|---|
| DeepNude | GitHub (now defunct) | It has been removed from the shelves. | GANs Synthesis |
| Nudify | GitHub | Open source, high risk | Batch synthesis |
| DeepNudePredict | GitHub | Community version | API open |
Warning: The vast majority of AI-powered striptease tools contain malicious programs that seriously threaten data security!
Limitations of AI-powered undressing technology
- 需A massive dataset of nude photosThe training data sources themselves are highly controversial.
- The generated results often contain distortions and flaws, and the technology is not yet perfect.
- Original image quality and pose limitationsThis results in obvious flaws in the generated effect.
Legal Risks and Ethical Challenges of Using AI-Powered Disrobing Tools
Major legal risks

| Types of legal risks | Current Status of Various Countries | Possible penalties |
|---|---|---|
| Infringement of portrait rights/privacy rights | Criminal prosecution is possible in many countries. | Victims may file charges, face fines, or be detained. |
| Production of harmful digital content | Strict regulations in Europe, America, Japan and other countries | Heavy fines or imprisonment |
| Deepfake Porn Image Creation | Taiwan, UK, US, South Korea | Children's Law, Copyright Law, Criminal Sanctions |
| Sexual extortion, cyberbullying | The penalty standards have been significantly increased. | Increased sentence, compensation for emotional distress |
- Creating, disseminating, or storing deepfake nude photos without consent is illegal.Taiwan's Criminal Code, the EU's GDPR, and the UK's Cyber Security Act all have explicit regulations on this matter, with maximum penalties including hefty fines, detention, and even criminal prosecution.
- International reports show thatAI-generated deepfake images of women undressing are widely used for sexual blackmail and revenge pornography.All of these are crimes.
Protection of Minors and People with Special Status
- Removing clothing from photos of children and teenagers constitutes a felony of Child Sexual Exploitation Images (CSAM).Whether or not it is disseminated, it is illegal.
- According to the IWF,AI-generated images of child exploitation surged in 2023.It has a huge social impact.
Legal advice for businesses and users
- Uploading your own or others' photos to unknown platforms can lead to misuse and make the data difficult to recover.
- Companies that develop, promote, or assist in the illegal distribution of such products will also be held liable.
- In addition to complying with the law, users also need to respect the right to know and the personal dignity of others.To avoid causing long-term harm due to momentary curiosity.
Protective measures and selection of legitimate AI image generation services
Advice on avoiding phishing and malicious attacks
- AI-powered stripping tools from unknown sources are highly likely to contain malware.This includes espionage, Trojans, ransomware, and the like.
- Download phishing versions of DeepNude and other programsThis could lead to the theft of passwords and cookies, or even extortion.
- 2024 Tech Case Study: Hackers use "DeepNude generator" to infect computer users on a large scale.
- Important: Keep your security software updated and stay away from unfamiliar software download links.

Recommended legitimate AI image generation services
| Tool Name | Link | feature | Prevention of unauthorized use |
|---|---|---|---|
| Midjourney | Midjourney | Text generation, compliant operation | Pornographic/nude content is prohibited. |
| DALL·E | OpenAI DALL·E | AI-generated art creations undergo strict content review. | Plain text filtering of nude photo keywords |
| Stable Diffusion | StabilityAI | Customizable models for formal applications. | Porn generation is blocked by default. |
| Canva AI | Canva | Image creative tools | Automatic filtering of nude photos |
It is recommended to use mainstream and compliant AI art/editing services to avoid getting involved in illegal photo synthesis or unauthorized tools.
User-centric safety and self-protection principles
Self-protection response to AI undressing technology
- Do not upload photos to unknown or unverified platforms.
- If your own or your relatives' photos are maliciously manipulated and spread, you shouldReport to the police immediately and contact the platform.Appeal.
- Make good use ofChildline removal serviceWe request that the offending images be removed.
Legal consultation and rights protection resources
- Victims can consult local legal aid centers or police authorities.
- Taiwan's online social media police stations, IWF, INHOPE, and other similar platforms all have channels for reporting cyberbullying.
- Parents or educators with concerns may refer to the following:Internet Matters Parents' SectionResponse guidelines.
Conclusion
With the exposure of AI-powered undressing tools and the improvement of regulations,Society is highly vigilant about the ethical and cybersecurity risks of synthetic images.Please do not try this out of curiosity, and do not create or distribute fake images. If you become a victim, you should...Seek legal and technical assistance as soon as possibleAI imaging technology will continue to advance, and we look forward to building a better future together with society.Moral bottom line and defense lineTo safeguard digital security and dignity.
© Copyright notes
The copyright of the article belongs to the author, please do not reprint without permission.
Related posts

No comments...